Which of the Following Are Not Consequences of Phishing
A Our zero liability policies apply only to unauthorized purchases and certain ATM transactions using your debit card. They may not be relied upon as authoritative interpretations.

Phishing Attacks What It Is And The Consequences Of An Attack Digital Brand Protection Fraudwatch
Any claims of unauthorized debit card purchases that do not meet the conditions of this section and any claims of unauthorized transactions involving.
. You may have no liability for unauthorized debit card purchases subject to the following terms and conditions. ADMINISTRATIVE EMPLOYMENT TAX EXEMPT ORGANIZATIONS. This revenue procedure provides a safe harbor that permits a taxpayer to exclude certain items from gross receipts under 448c and 6033 of the Internal Revenue Code Code as applicable solely.

This Is A Grammar Review About Two Types Of Verbs Followed By Either Ing Or Infintive The First Type Is The One Where Grammar Worksheets Types Of Verbs Verb

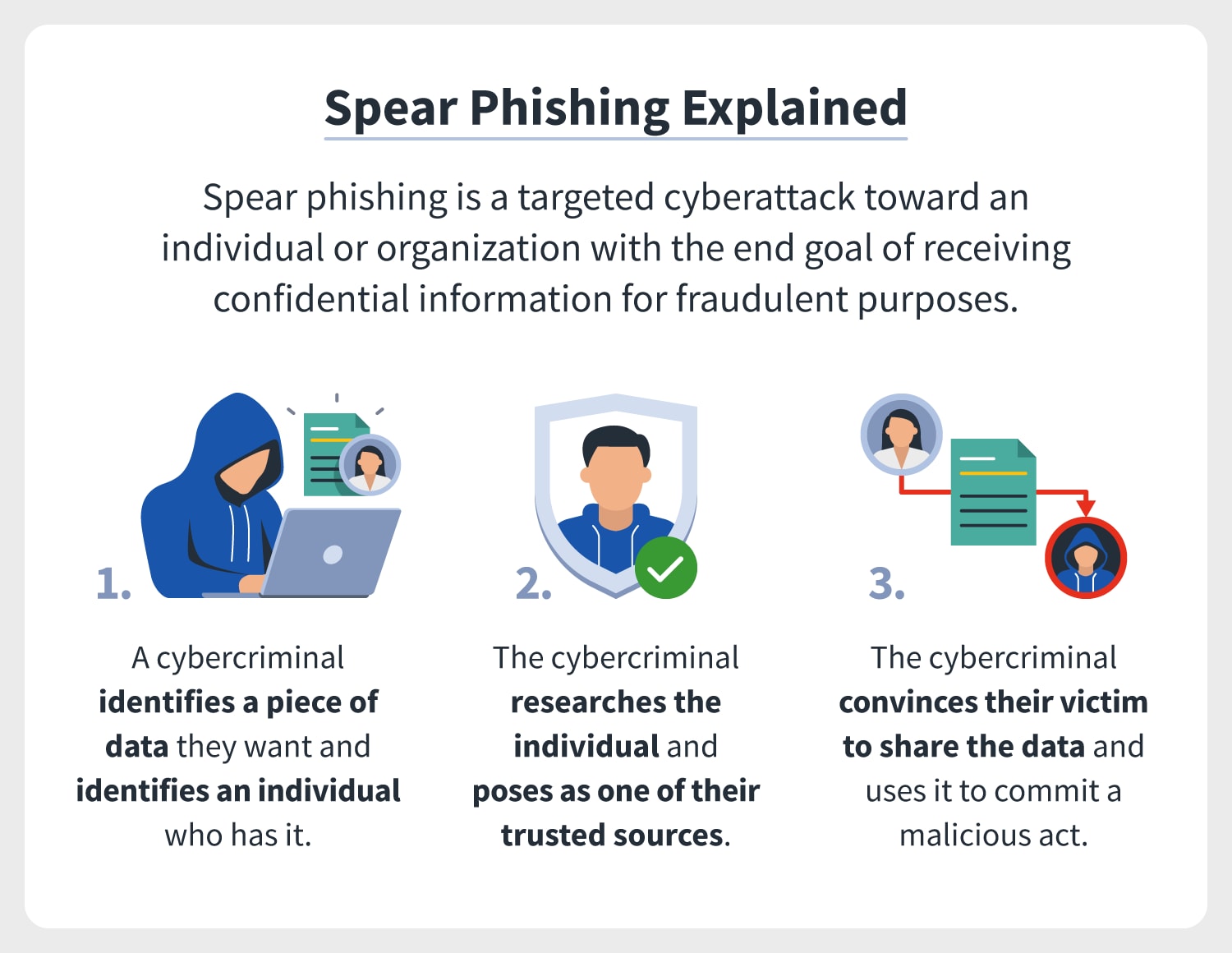
Spear Phishing A Definition Plus Differences Between Phishing And Spear Phishing Norton

Beware Of Phishing Attacks Data Loss Prevention Data Loss Data
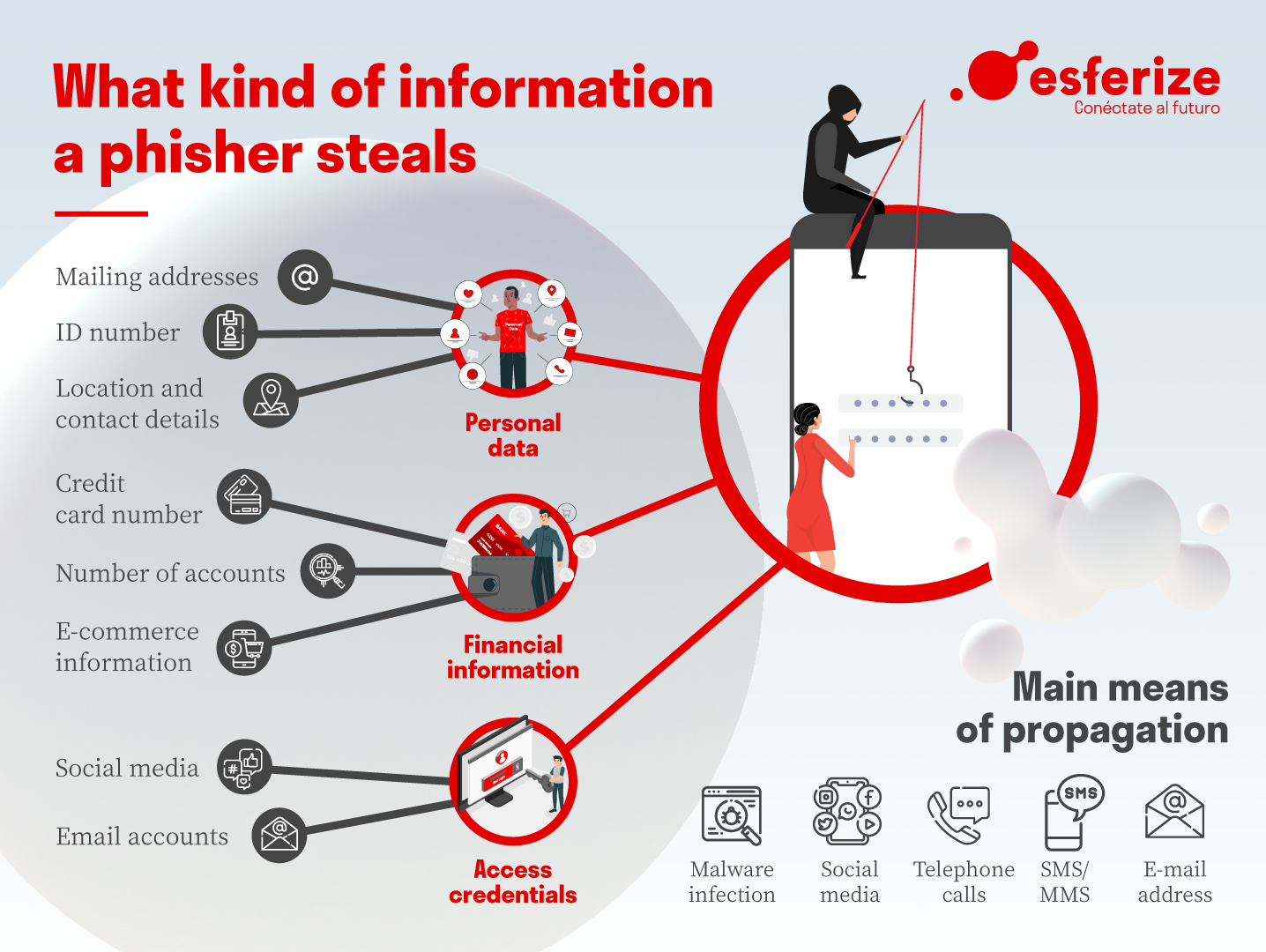
What Is Phishing How Does It Work And How To Protect Yourself Esferize

6 Common Phishing Attacks And How To Protect Against Them

Security Experts On How To Prevent Social Engineering Attacks Including The Latest Techniques Prevention And Real Worl Policy Template Engineering Awareness

9 Easy Ways To Lose Your Cryptocurrency Cryptocurrency Blockchain Cryptocurrency Cryptocurrency Trading

Long Term Effects Of Data Breaches And Their Financial Consequences Data Breach Data Cyber Security Awareness

Hello Dear Customer Says Phishing Email Sayings Hello Dear Accounting Information

Email Address Updated Says Phishing Email Email Address Sayings Email

Here S Everything You Need To Know About Whatsapp S New Privacy Policy In 2021 Privacy Policy Policies Latest Technology News

Adobe Illustrator Arrow Key Is Not Working 100 Fixed Illustrator Tutorial Yout Illustrator Tutorials Adobe Illustrator Adobe Illustrator Tutorials

6 Common Types Of Phishing Attacks

4 Ways To Spot Fake Emails Email Security Cyber Security Awareness Managed It Services

Security Awareness Poster Used To Educate People On How To Recognize Fake Cyber Security Education Information Technology Humor Cyber Security Awareness Month




Comments
Post a Comment